Curious about how to hack someone’s phone remotely without touching it in 2024? Look no further. Whether it’s concerns about a relationship or keeping an eye on your children’s online activities, you can access their phone remotely from your device or computer for added peace of mind. While constant monitoring isn’t feasible, spy software allows you to track phone activity without detection discreetly. Let’s dive into how to hack someone’s phone in 2024 remotely.
Key Takeaways:
- When it comes to hacking someone’s phone without touching it, mSpy stands out as a reliable option. It offers comprehensive monitoring capabilities, including GPS tracking and access to social media messages.
- Be cautious of random apps from online searches, as they may attempt to compromise your data.
- Always use phone monitoring software for ethical purposes to avoid potential legal consequences. Stay informed and responsible when considering such actions.
>> Don’t Miss:
- How to Clone a Phone Without Touching It in 2024
- How To Track Someone Location With Phone Number in 2024
- How to Track an Android Phone from an iPhone in 2024? (6 Methods)
- How to Track an iPhone from an Android Phone in 2024? (8 Solutions)
- How to Mirror A Phone to Another Phone Without Them Knowing in 2024
Reasons Why People Hack Someone’s Phones
Here are the three most common reasons for mobile phone hacking:
- Keeping Your Kids Safe: In today’s digital age, parents often worry about their children’s safety, especially when they have access to cell phones. There are concerns about online predators and the sharing of private information among peers. Some parents resort to hacking their children’s phones to monitor their whereabouts and online activities to ensure their safety.
- Security for Your Company: Businesses that provide company phones to employees may want to know how to hack an Android phone remotely for monitoring purposes. This allows employers to track employee locations and phone activities, including photos, to ensure smooth business operations and reduce the risk of misconduct in the workplace.
- Personal Reasons: While phone hacking is unethical, some individuals engage in it to spy on their partners, friends, or coworkers. Such actions represent a severe breach of privacy and can have significant consequences for relationships and trust.
It’s important to note that hacking someone’s phone without their consent is illegal and unethical, and it can lead to serious legal consequences. Privacy and trust should be respected in all personal and professional relationships.
How To Hack Someone’s Phone Remotely (14 Methods)
Phone hacking might seem like a mystery, but it often involves a mix of technical skills and social manipulation. Here’s a closer look at some common techniques about how to remotely hack someone’s phone:
Method 1: Use a Spying App (EyeZy and mSpy)
Phone tracking software offers a discreet way to access someone’s phone without physical contact or computer hacking skills. Among these options, the EyeZy and mSpy stand out as excellent choices for various monitoring purposes.
mSpy – Best Phone Hacking App for iPhone
Using hacking software like mSpy is a common way to remotely hack someone’s iPhone or Android phone. Originally designed for parents to ensure their children’s safe use of technology, mSpy has become popular among others for its ease of use and helpful features.
For a comprehensive understanding of its capabilities, delve into our comprehensive mSpy review.
To use mSpy:
Install mSpy: Begin by installing mSpy on the target device.
Select Device Type: Choose the type of device you want to monitor, whether it’s an Android or iOS device.
Download the App: Download the mSpy app on your mobile device, then follow the on-screen instructions to configure it.
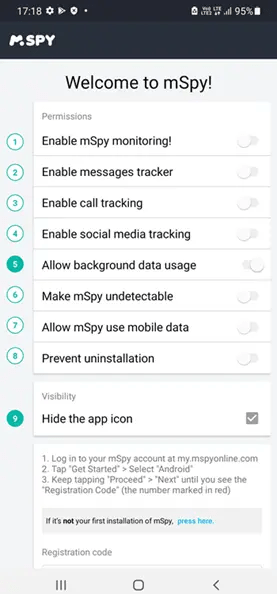
Note: Physical access to the person’s phone is necessary to set up mSpy.
- Access Dashboard: After setup, you can access the dashboard and start tracking calls, text messages, and photos taken by the phone’s owner. It can also store passwords for websites they visit.
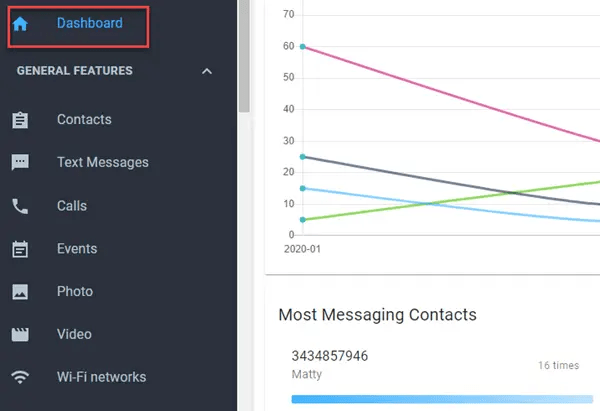
EyeZy – Best Phone Hacking App for Android
EyeZy provides extensive capabilities, including user monitoring and location tracking. It can gather data from multiple sources, such as cellular networks, location services, email, and popular social media platforms like Facebook and WhatsApp. What makes EyeZy exceptional is its ability to spy on a phone without arousing suspicion in the owner. >>Check eyeZy review
To hack a phone remotely using EyeZy in 2024, follow these simple steps:
- Register with your email address, and remember your login credentials.
- Enter the target phone’s details and select the Android icon for setup.
- Gain access to the target device and adjust the settings. Ensure that you enable the installation from unknown sources to install spy monitoring software.
- EyeZy will infiltrate the target device during installation, allowing you to monitor its activities from your dashboard. If you choose to “start monitoring,” the program will operate discreetly without the user’s awareness.
- Use the mobile device’s web browser to access the dashboard and explore its features. The target device will send you real-time data.
EyeZy offers a free trial for those considering its services. If you encounter any issues, their support team is readily available through a live chat feature on their website to assist you promptly. Once you experience EyeZy’s capabilities, you may find it to be the only phone monitoring software you need.
Method 2: Use a Stingray or IMSI Catcher
The IMSI Catcher, commonly known as Stingray, is a device resembling a small cell phone tower. When activated, it attracts phone devices within a specific radius to connect to it. This allows the user to obtain the unique IMSI number located on the target’s SIM card. The use of IMSI Catchers is subject to strict regulations, and they are primarily designed for hacking into GSM devices.
While IMSI Catchers are not readily accessible to the general public, there are smaller, less powerful variants available that can operate within a limited area for tracking purposes. Once the IMSI code is acquired, it can be processed through a Python script to collect data discreetly from the target’s mobile phone.
However, it’s essential to note that this method is highly questionable and unreliable. Using a Python script obtained from GitHub is possible, but it requires technical expertise. Additionally, attempting to use IMSI Catchers or similar devices may lead to legal consequences and should only be considered by those with a deep understanding of the associated risks.
Method 3: Phishing Attacks
A phishing attack is a cyber trick where the attacker sends a misleading link to the target person. When the target clicks on the link, it can either download harmful files or send their personal information to the hacker. These attacks often succeed because the links seem harmless at first glance.
You can remotely hack someone’s phone using a phishing attack. Here’s how it works: You send the person an iMessage or text message with a convincing story. The goal is to make them believe the message, so they willingly give away private information like passwords. Once you have their information, you can use it for various purposes. Keep in mind that not everyone will fall for this, but it’s one way to attempt to hack Android or iPhone devices.
Method 4: Bluetooth Hacking
Bluetooth technology has made connecting our devices more convenient. It allows us to link our phones with cars, TVs, and other gadgets for efficient tasks like making calls and playing music. Another way to remotely hack someone’s phone is through Bluetooth hacking.
The interesting thing about this method is that you don’t always need physical access to the target phone. Here’s how you can use Bluetooth technology to hack into someone’s phone:
- Check if the target device has Bluetooth connectivity.
- If Bluetooth is off, either activate it yourself or convince the owner to do so.
- Establish a Bluetooth connection with the phone to gain access to its information and data.
- Download the desired data while staying within 30 feet of the phone.
A tip to protect your own phone from hacking: Never connect to unknown Bluetooth devices. While it might be accidental, it could also be a hacking attempt.
Method 5: Wi-Fi Attacks
Just like how Bluetooth can be a way for hackers to get into your phone, they can also use Wi-Fi. Especially when you’re on public Wi-Fi networks, there’s a risk. Sometimes, these networks might be set up by bad people waiting for you to connect so they can do harm. To be safer, you should change the default password for your home Wi-Fi so that hackers can’t easily get in.
When you’re using public Wi-Fi, you can protect yourself by setting up something called a “mobile VPN” on your iPhone or Android. This VPN thing is like a secret code that makes your connection super secure, so bad people can’t sneak into your phone.
Wi-Fi is an essential part of modern life, and it can also be used to perform man-in-the-middle attacks on someone’s phone. If this method is of interest to you, here’s how you can carry out these attacks:
- Step 1) Set up a fake Wi-Fi access point.
- Step 2) Ensure that the access point is positioned near the target device to appear legitimate.
- Step 3) Wait for the target to connect to the network.
- Step 4) Redirect them to your app or website as the hacker.
- Step 5) Gain access to information transmitted over this network and use it as you see fit.
- Step 6) Optionally, install malware or spy software to gain greater control over their device.
Method 6: Midnight Raid
The “Midnight Raid” method is a relatively simple way to hack a phone without the need for spyware installation. To perform this method, a hacker typically requires a laptop with Wi-Fi connectivity and two phones: one phone serves as a GSM modem for the laptop, and the other phone receives information.
Here’s how the Midnight Raid works:
- The attack is usually carried out during the night while the target user is asleep, and the cell phone is left unattended or charging on a side table.
- The hacker sends a text message to the target phone at midnight, often with a message like “You are being hacked.”
- This text message triggers the Internet Explorer (or another browser) on the target device when it receives the text.
- An application is then executed on the target phone to retrieve data.
- The SMS message returns to the phone from which the text was sent and brings with it the phone’s unique ID, known as its IMSI number.
- The application can then steal various types of information from the target device. In some cases, the hacker may use this method to push viruses to the device or initiate a denial of service (DDOS) attack.
It’s important to note that this method relies on exploiting vulnerabilities in the target phone’s software and may not work on all devices. Additionally, hacking someone’s phone without their consent is illegal and unethical. It’s essential to respect privacy and adhere to laws and regulations when dealing with digital devices and information.
Method 7: Spam Message Hacking
Spam messages are a common and deceptive method used to hack cell phones. These messages often appear harmless and clutter our inboxes regularly, making them easy to overlook or delete. However, they can pose a significant threat as hackers can use them to gain access to sensitive information stored on people’s phones.
Spam emails serve as a potential entry point for hackers, allowing them to compromise email accounts and steal valuable data, such as email addresses and contacts saved in Google accounts. This method can be employed to hack into someone else’s phone without their knowledge or consent.
To execute this approach, you can initiate the process of resetting a Google account password. This involves visiting the Google account login page, selecting the “forgot password” option, and entering the phone number associated with the target’s account. Limited access to the Google Account can be obtained by entering the verification code sent to the linked phone number.
If you have access to a user’s account, you can change their password, effectively locking them out. Instead of alerting them to the compromise, you may opt to secretly monitor their conversations to verify any suspicions you may have. However, it’s essential to remember that engaging in such activities without consent can have legal and ethical implications.
Method 8: SIM Card Swapping
Every Android and iPhone is equipped with a SIM (subscriber identity module) card. Swapping the SIM card is a method hackers use to access information on someone’s phone. They contact a mobile carrier, such as Verizon or T-Mobile, to obtain a new SIM card, deactivating the old one in the process.
With the new SIM card in place, hackers gain control over the person’s phone. This allows them access to phone calls, text messages, and more. However, it’s worth noting that this method is not commonly used by parents to monitor their children’s phones.
Method 9: Social Engineering
Social engineering isn’t limited to hacking phones; it’s a tactic used to influence human interactions for a specific outcome through deception or manipulation. While social engineering has legitimate uses, it has become a method for hackers to access other people’s devices. It can be employed for monitoring purposes, such as checking on your kids or partner.
Here are some ways to use social engineering to hack a phone:
- Phishing schemes deceive users into divulging personal information, like banking details.
- Malvertising involves inserting malware into digital advertisements. When users click on a legitimate ad, they become infected with malware.
- Smishing schemes are a type of phishing attack conducted through text messages.
- In-person social engineering involves interacting with someone to convince them to share their password, allowing access to their phone and activities.
Method 10: Malvertising
Malvertising combines advertisements and malware to deceive users. Malware is harmful, and people usually don’t willingly install it on their devices. Malvertisers try to trick individuals into clicking on their advertisements.
When users click on these deceptive advertisements, often offering something for free, it can trigger the download of malware onto their devices. Once this malicious software is installed, hackers gain the ability to spy on the user’s activities, including text messages, phone calls, and photos. This spying can also help them obtain sensitive information like passwords.
Method 11: Pretexting
Pretexting is a form of social engineering that involves using fabricated pretexts to engage with someone and extract their personal details. Here are a few examples of pretexting methods that individuals might use to gain access to a phone or other personal information:
- Pretending to have won the lottery and needing access to an account to send the prize money.
- Claiming to require a verification code due to the loss of their phone.
These are just a couple of examples of pretexting attacks, and there are many more variations. Some pretexting attempts may occur through text messages, while others might use social media messaging platforms.
Method 12: Charging Stations
Be cautious when using public charging stations, as some can infect your phone with malware in a practice known as “juice jacking.” This malware can monitor your activities, collect and transmit private data, and even make unauthorized transactions.
Method 13: Trojans
Trojans disguise themselves as harmless apps or files to deceive users. Once opened, they can spy on you, create backdoors, use your phone in a botnet, or send malicious SMS messages. Trojans are particularly tricky because they aim to gain your trust and go unnoticed.
Method 14: Cryptojacking
Cryptojacking involves the unauthorized use of a device to mine cryptocurrencies like Bitcoin. Hackers secretly install crypto mining malware on your phone, using its resources to mine cryptocurrency and send it to their digital wallet.
Protecting your phone from these threats is crucial. Remember, understanding these techniques can help you stay vigilant against potential phone hacking attempts.
Which Phone Is Easier To Hack: Android or iPhone?
More people use Android phones than iPhones, so hackers often go after Androids. But iPhones can still get hacked. Think of it like how Macbooks can sometimes get viruses.
The reason Android phones are easier to hack is because the Android system is more open. It’s like having a door that’s a bit open. On the other hand, iPhones are harder to hack because their system is like a locked box. Apple doesn’t share its secrets with app makers, and it’s tough for hackers to mess with iPhones.
Android, made by Google, is open, like having an open book. This openness lets app makers do more things with it. But it also means Androids can be easier to hack.
No matter what phone you have, always keep it updated to fix problems and make it safer. And only get apps from trusted places like Google Play or Apple’s App Store. That way, you’re less likely to get hacked.
How to Tell If Someone Hacked Your Phone? Common Signs
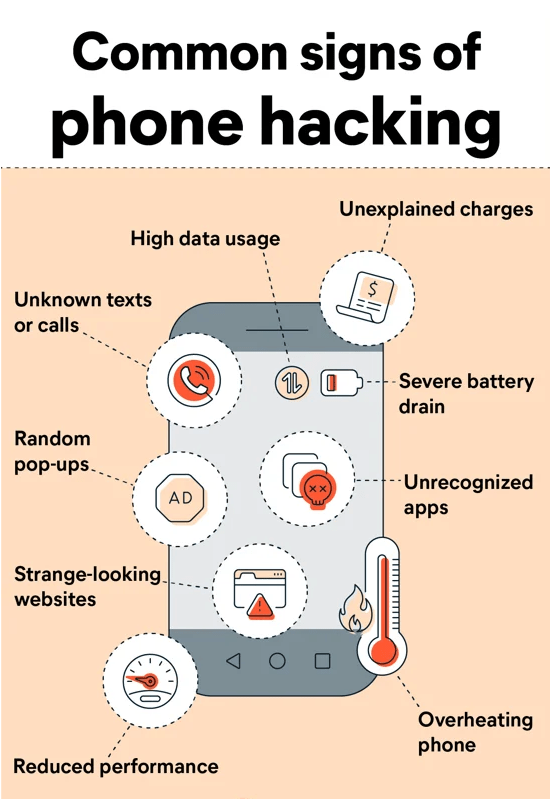
Is your phone acting weird? Here’s how to know if someone hacked your phone:
- Pop-up Intrusion: An influx of pop-up ads could signal an adware infection. Avoid clicking on these pop-ups, as interacting with them can worsen the issue.
- Unfamiliar Communications: Receiving messages or calls from unknown numbers may suggest a data breach. Avoid answering calls from unrecognized sources unless their authenticity is verified.
- Unexpected Data Surge: A sudden increase in data usage without a change in your online activities can be a red flag. Malicious apps running in the background might be consuming data. Review your apps and remove suspicious ones.
- Excessive Battery Drain: If your phone’s battery depletes rapidly, it could be due to unwanted apps draining resources. Malware or hacking might be the cause.
- Overheating: Unexplained overheating, even when the phone is idle, could be attributed to malicious software.
- Sluggish Performance: Frequent dropped calls, undelivered texts, crashes, or unexpected reboots may indicate malware or background apps compromising performance.
- Altered Web Experience: Malware-infected phones can redirect users to unsafe websites. If websites appear unfamiliar or suspicious, exercise caution.
- Unexpected Charges: An unusually high phone bill might result from rogue apps increasing data usage. Be wary of fleeceware apps and promptly cancel unwanted subscriptions.
- Unknown Apps: Unrecognized apps appearing on your phone may indicate a hack. While some pre-installed apps (bloatware) may be unfamiliar, unusual additions warrant attention.
Keep in mind that not all issues result from hacking; some could stem from phone aging or limited storage space. Stay observant but avoid jumping to conclusions.
What To Do If Your Phone Is Hacked
If you suspect that your phone has been hacked, immediate action is essential to minimize potential damage. Here’s a step-by-step guide on what to do:
- Disconnect From the Internet: To sever any potential connections between your phone and the hacker, turn off Wi-Fi and mobile data. This prevents further access to your device and data theft.
- Remove Suspicious Apps: Uninstall any recently installed apps or unfamiliar ones that may have triggered the hacking. These apps could contain malware or be part of the problem.
- Run an Anti-Malware Scan: Consider running a scan using a reputable anti-malware or antivirus application. These tools can detect and remove malware on both Android phones and iPhones. There are several excellent free antivirus apps available for this purpose.
- Factory Reset Your Phone: If the issue persists, performing a factory reset on your phone may be necessary. This action resets system settings, removes self-installed apps that may be infected, and helps eliminate malware. However, be aware that a factory reset erases all your data, so ensure you back up important files and apps before proceeding.
If your phone is hacked and you really need to restore it, here’s how to do it:
For iPhone:
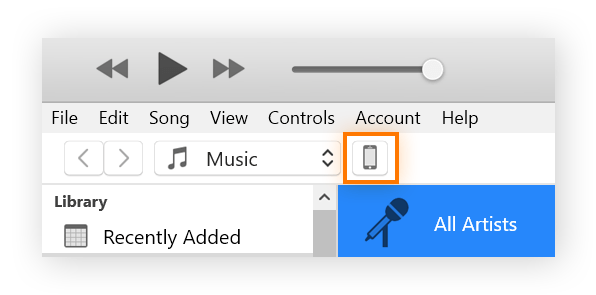
- Connect your iPhone to your computer using a USB cable.
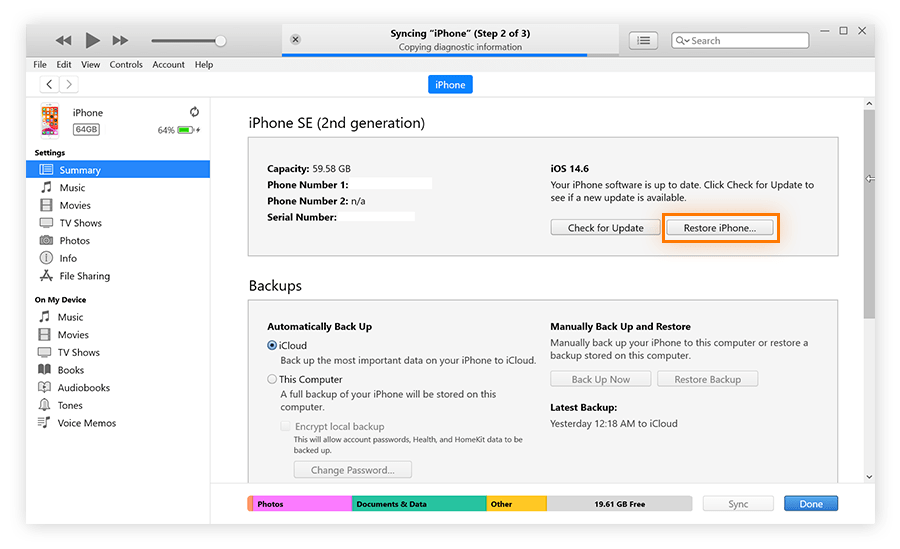
- Open iTunes and click on the iPhone icon.
- Look for the “Restore iPhone” option and click it.
- Follow the instructions on the screen to reset your iPhone.
For Android:
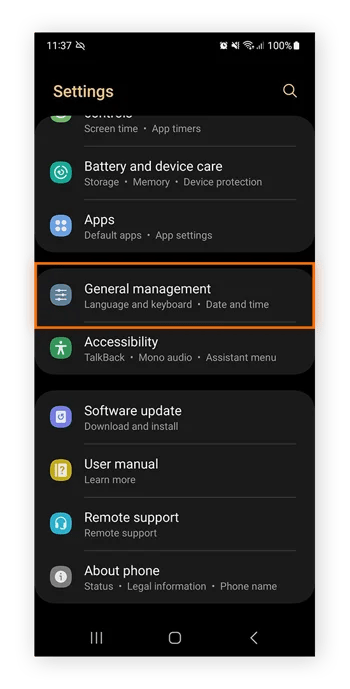
- Go to your phone’s Settings.
- Look for “General Management” or something similar.
- Tap on “Reset,” and then select “Factory Data Reset.”
- Confirm by tapping “Reset.”
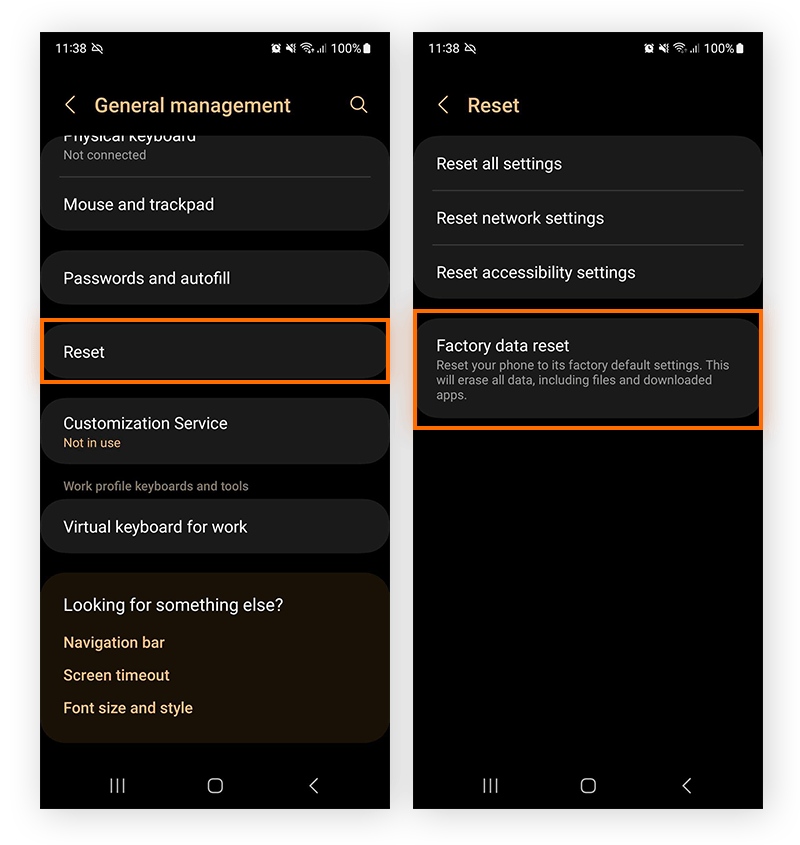
Just remember, this is a last resort because it erases everything on your phone. So, be absolutely sure before you do it.
- Change Your Passwords: If your phone gets hacked, the first thing to do is change your passwords. This includes your phone’s access code and all the passwords for your accounts linked to your phone, like social media, online banking, and cloud services. Make sure these new passwords are strong to prevent future hacks.
- Inform Your Contacts: Your hacked phone might have sent weird messages or emails to people you know, so tell your contacts about it. Warn them not to click on any strange links or messages to avoid falling victim too.
- Contact Your Service Provider: Get in touch with your mobile service provider because a hacked phone could be redirecting your calls and texts to the hacker. They can stop any unauthorized activity, secure your phone number, and add extra security measures like a PIN or security question.
By following these steps promptly, you can take control of the situation, protect your personal information, and restore the security of your compromised phone.
How To Protect Your Phone Against Hacking
The most effective way to safeguard your phone against hacking is through prevention. Preventing a cyberattack is far easier than dealing with the aftermath. Here are 10 tips to prevent remote hacking of your phone:
- Keep Your Phone and Apps Updated: Regularly install operating system and app updates. These updates often include crucial security patches to address newly discovered vulnerabilities.
- Use Strong Passwords: Ensure that you use robust, unique passwords for your accounts. Enable Two-Factor Authentication (2FA) whenever possible to add an extra layer of security.
- Employ a VPN (Virtual Private Network): A VPN encrypts your internet traffic, safeguarding your data, especially when using public Wi-Fi networks. This helps protect your information from potential eavesdroppers.
- Clear Your Cache: Regularly clear your cache on both Android and iPhone devices. Hackers can target sensitive data stored in your cache or inject malicious code into it.
- Minimize Stored Personal Data: Limit the amount of personal data stored on your phone. The less sensitive information your device holds, the less enticing it is to hackers.
- Disable Wi-Fi and Bluetooth When Not in Use: Close potential security loopholes by turning off Wi-Fi and Bluetooth when you’re not actively using them.
- Change Your SIM PIN: Hackers can exploit default SIM card PIN codes. Change your SIM PIN to a unique and secure one to prevent unauthorized access to your SIM card and mobile network.
- Beware of Public Charging Stations: Public charging stations may hide dangers. Some hackers compromise these stations with malware, stealing your passwords and personal data. Carry a portable power pack instead.
- Encrypt Your Phone: Encryption safeguards your calls, messages, and critical data. Check if your phone is encrypted, or enable it in your settings.
- Stick to Official App Stores: Download apps only from trusted sources like Google Play and Apple’s App Store. These platforms vet apps for safety, reducing the risk of malicious downloads compared to third-party stores.
- Avoid Jailbreaking: Jailbreaking or rooting your phone means changing its core software to bypass rules set by developers or manufacturers. This can open up your phone to more risks. When you modify your phone’s operating system this way, you lose the built-in security, making it easier for hackers to attack your phone and install malicious software.
By following these tips, you can significantly reduce the chances of falling victim to remote phone hacking and keep your personal information secure.
FAQs
When it comes to remotely tracking a cell phone without touching it, there can be many doubts in your mind. Here we address the most common ones:
Can a Phone Be Hacked When Turned Off?
Powering off your phone can prevent most hacking attempts since without an internet connection, malicious code usually can’t execute. However, some of the latest iPhone models don’t fully turn off when powered down. Instead, they enter a low-power state, which allows features like Find My iPhone to work. While this can be useful, it might also pose a potential risk if hackers find ways to exploit this feature in the future.
Can Your Phone Camera Be Hacked?
Yes, your phone’s camera can be hacked, but the chances are low if you follow these steps:
- Check and control app permissions for camera access.
- Keep your phone’s operating system updated.
- Download apps only from official app stores.
- Avoid clicking on suspicious links.
- Consider covering your camera when not in use for added security.
Can Someone Hack My Phone By Calling Me?
While it’s relatively uncommon for your phone to be hacked directly through a phone call, calls can be a component of broader hacking or social engineering schemes. Phone-based phishing, also known as vishing, involves attackers impersonating legitimate entities or IT support to deceive you into disclosing sensitive information, such as login credentials or credit card details. This stolen data can then be exploited for various types of hacks. Remain cautious and verify the legitimacy of any unexpected calls to safeguard your personal information.
Can You Get Hacked Through WhatsApp?
Hacking through WhatsApp is possible if you click on a harmful link or attachment. Surprisingly, even accepting a WhatsApp call can, in theory, introduce malware to your phone. So, exercise caution when dealing with calls or messages from unfamiliar numbers. It’s crucial to keep your WhatsApp app updated to ensure you have the latest security protections.
Can My Phone Be Hacked Via Text Message?
Indeed, your phone can fall victim to hacking through text messages. Cyber attackers employ various tactics, including sending deceptive links or attachments via text messages. Once these are clicked or downloaded, malware can infiltrate your device, potentially leading to unauthorized access and data theft. Stay vigilant and cautious when handling text messages to protect your phone’s security.
Can Someone Hack Into My Phone Remotely?
Yes, your phone can be hacked remotely, but only if someone had physical access to your phone and installed monitoring software on it. This software would allow them to access your phone’s camera and potentially spy on you.
Can Someone Hack Into My Phone Without Touching It?
EyeZy and similar tracking apps enable remote access to a target’s phone without the need for physical access.
These applications can be used to discreetly monitor a person’s online activities.
>> Don’t Miss:
- How to Hack Someone’s Discord Account In 2024
- How To Hack Someone’s Snapchat Account in 2024: 8 Ways
- How to Track My Wife’s Phone Without Her Knowing in 2024
- How To View Private Twitter Account Without Following in 2024
- How to View Private TikTok Accounts In 2024? (100% Working 7 Methods)
Conclusion
We’ve demonstrated various methods of how to hack someone’s phone remotely without touching it.
The most straightforward and effective approach is to utilize a third-party phone monitoring application like mSpy or EyeZy.
This option not only delivers exceptional efficiency at an affordable cost but also prioritizes the security of your personal data.
>> Learn more how-to guides on phone app solutions.





